Keycloack
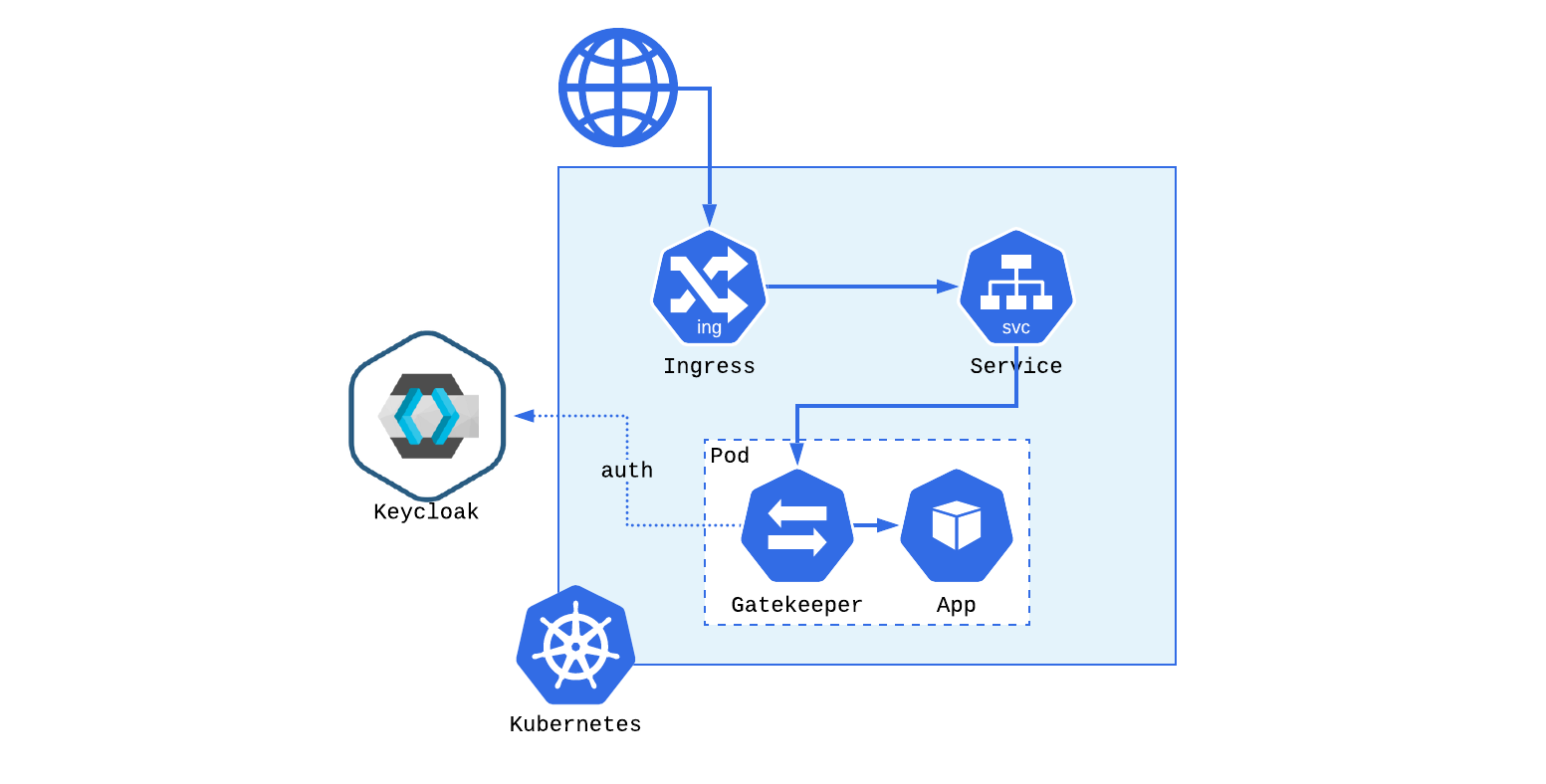
Identity Provider (IdP) Open Source con soporte para OIDC (OpenID Connect) o SAML.
✅ Soporta OIDC, OAuth2 y SAML.
✅ Se integra con LDAP/Active Directory para usuarios corporativos.
✅ Tiene un panel de administración web para gestión de identidades.
✅ Puede delegar autenticación en Google, GitHub, Microsoft, etc.
✅ Se despliega fácilmente en Kubernetes con un Helm Chart o manifiestos YAML.
Implementación
# Añade el repositorio
helm repo add codecentric https://codecentric.github.io/helm-charts
helm repo update
# Instalación
helm install keycloak codecentric/keycloak \
--namespace keycloak --create-namespace \
--set golbal.storageClass=nfs-client \
--set postgresql.enabled=true \
--set postgresql.persistence.enabled=true \
--set postgresql.persistence.storageClass=nfs-client \
--set keycloak.service.type=ClusterIP \
--set ingress.enabled=true \
--set ingress.ingressClassName=nginx \
--set ingress.hosts[0]=sso.k8s.ictiberia.com
--set ingress.tls=true \
--set ingress.selfSigned=true
# Unistall
helm delete keycloak -n keycloakNamespace
apiVersion: v1
kind: Namespace
metadata:
name: keycloakPVCs
PostgreSQL
---
apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: postgres-pvc
namespace: keycloak
spec:
accessModes:
- ReadWriteOnce
resources:
requests:
storage: 10Gi
storageClassName: nfs-clientKeycloak
---
apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: keycloak-pvc
namespace: keycloak
spec:
accessModes:
- ReadWriteMany
resources:
requests:
storage: 5Gi
storageClassName: nfs-clientStatefulSet PostgreSQL
---
apiVersion: apps/v1
kind: StatefulSet
metadata:
name: postgres
namespace: keycloak
spec:
serviceName: postgres
replicas: 1
selector:
matchLabels:
app: postgres
template:
metadata:
labels:
app: postgres
spec:
containers:
- name: postgres
image: postgres:15
env:
- name: POSTGRES_DB
value: "keycloak"
- name: POSTGRES_USER
value: "keycloak"
- name: POSTGRES_PASSWORD
value: "keycloakpassword"
ports:
- containerPort: 5432
volumeMounts:
- name: postgres-storage
mountPath: /var/lib/postgresql/data
volumes:
- name: postgres-storage
persistentVolumeClaim:
claimName: postgres-pvcDeployment Keycloak
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: keycloak
namespace: keycloak
spec:
replicas: 2
selector:
matchLabels:
app: keycloak
template:
metadata:
labels:
app: keycloak
spec:
containers:
- name: keycloak
image: quay.io/keycloak/keycloak:latest
args: ["start"]
env:
- name: KC_DB
value: "postgres"
- name: KC_DB_URL
value: "jdbc:postgresql://postgres.keycloak.svc.cluster.local:5432/keycloak"
- name: KC_DB_USERNAME
value: "keycloak"
- name: KC_DB_PASSWORD
value: "keycloakpassword"
- name: KEYCLOAK_ADMIN
value: "admin"
- name: KEYCLOAK_ADMIN_PASSWORD
value: "adminpassword"
ports:
- containerPort: 8080
volumeMounts:
- name: keycloak-storage
mountPath: /opt/keycloak/data
volumes:
- name: keycloak-storage
persistentVolumeClaim:
claimName: keycloak-pvcServicios
PostgreSQL
---
apiVersion: v1
kind: Service
metadata:
name: postgres
namespace: keycloak
spec:
ports:
- port: 5432
targetPort: 5432
selector:
app: postgresKeycloak
---
apiVersion: v1
kind: Service
metadata:
name: keycloak
namespace: keycloak
spec:
ports:
- port: 80
targetPort: 8080
selector:
app: keycloakIngress
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: keycloak-ingress
namespace: keycloak
annotations:
nginx.ingress.kubernetes.io/rewrite-target: /
cert-manager.io/cluster-issuer: "letsencrypt-staging" # Cambiar a "letsencrypt-production" en producción
spec:
ingressClassName: nginx
tls:
- hosts:
- sso.k8s.ictiberia.com
secretName: keycloak-tls
rules:
- host: sso.k8s.ictiberia.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: keycloak
port:
number: 80Comandos
# Verificar el despliegue
kubectl get pods -n keycloak
kubectl get svc -n keycloak
kubectl get ingress -n keycloak
